On This Page
Security Violations Report
Overview
|

|
The Security Violations report provides a detailed summary of all security policy violations detected within the selected domain, device, and Unified Security Policies (USPs).
Security Violations includes violations such as violated security policies, violated rules, and the critical levels of each violation.
This report enables you to:
-
Identify security gaps
-
Prioritize rules for remediation, removal or exception review
-
Ensure consistent awareness of violations by the relevant team
What Can I See Here?
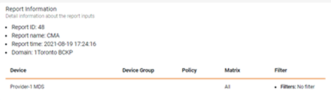
Report Information
The report header includes details with the report ID, name, time, domain, and the device information.
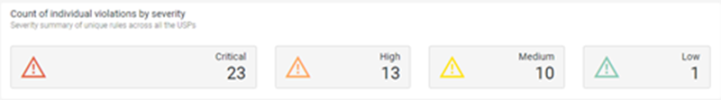
Violations by Severity
This section displays a summary of the count of individual violations by severity.
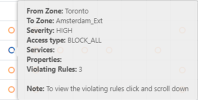
USP Violations
This section displays the violating rules, by severity, for each USP.
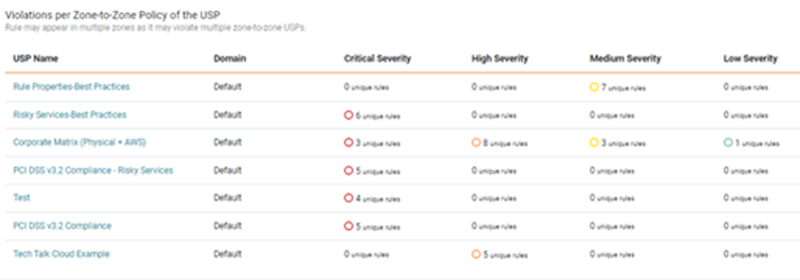
You can click a USP Name to see the matrix for violations for each severity level.
You can hover on a violation circle to see details for that violation.
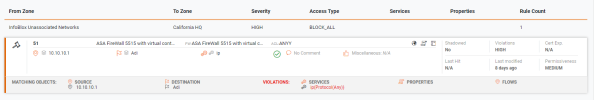
When you select one or more violations, you will see the details of the rules with violations under the matrix.
Violations and matching objects for the violations appear for each rule.
You can also select a severity level for the entire USP to see all rules with violations for that level.
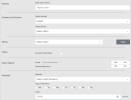
Create a Security Violations Report
Prerequisites
-
In the Settings > General page, the administrator must configure the outgoing SMTP server and the remote repository.
Procedure
-
From the Create (
 ) menu, click Security Violations.
) menu, click Security Violations.The Setup page for the report appears.
-
Complete the report fields:
-
General: Report name.
-
Domains and Devices: Select a domain and one or more devices or device groups.
-
Matrix: After selecting a domain, select one or more USPs.
-
Filters: Excludes rules based on filters. Select the check box and provide values for filter components.
A filter definition excludes rules according to the value of the following components:
Filter Component
Description
Example
Source/Destination Source and Destination an IP ( 1.1.1.1), subnet (1.1.1.0/24), oranyService Service tcp:80 Action
Comment Partial or full text from comments in the rule Production environment Tag name (Palo Alto only) Source/Desitnation Device Zone In a single filter definition, the filter components are logically joined using the AND operator. In this example, a rule will be excluded if it has
anyin the source and2.2.2.2in the destination.You can create additional filter definitions. STRE treats the relation between filter definitions with an OR operator. In this example, a rule will be excluded if it has a source value of
1.1.1.1or destination value of2.2.2.2.
-
Export Report:
-
Email: Specify the recipients for notification emails. Press Tab or Enter to separate multiple email addresses.
The email message contains a link to the report in STRE. Reports can be generated as PDF or CSV files, and you can select either option or both (if enabled) to include in the email as an attachment. If the report file is larger than 4 MB, the attachment is compressed as a
.zipfile. -
Remote Repository: STRE can export reports using SFTP. Specify the report format - PDF or CSV.
If the report finished successfully, you can verify that the new files appear in the Reports Folder path, in the remote repository, configured by your administrator (see Send Reports Using SFTP).
-
- Schedule: Configure the following:
- Repeats: Select the frequency by which the report should run. Options include Daily, Weekly, and Monthly.
- Days of the week: Select one or more days on which the report should run.
- Time: Indicate the time at which the report should run.
When scheduling a report to run on a monthly basis, you must choose a single Day of the week value. For whichever weekday you choose (Mon, Tues, Wed, etc.) the report will run on the first of that day every month. Keep in mind, this may not correlate with the first calendar day of that month.
-
-
Click one of the following:
 : Saves the report. The Saved menu lists all saved and scheduled reports.
: Saves the report. The Saved menu lists all saved and scheduled reports. : Runs the report. After a report runs, you can view the results in the Repo menu.
: Runs the report. After a report runs, you can view the results in the Repo menu.
Available Report Formats
When viewing the report output, use the Export menu to save the report data.
You can save the data for this report as a CSV file, a PDF output file, or an offline HTML file.
-
The CSV export option is useful when you want to create your own reports based on the specific data from the report configuration. The CSV contains the networks, which are part of the violations, as data points.
-
When you select PDF, check the Export menu again for the PDF is ready status and click the link to view the PDF output. The PDF output has been redesigned and is now saved as a document file.
-
The offline HTML file, which you download as a static HTML file, includes all of the report data.