On This Page
Overview
An asset in SecureCloud is a resource in your cloud account such as a virtual machine, database, bucket storage, or Kubernetes cluster that will be displayed in SecureCloud if granted access. Multiple assets connected by a load balancer may be represented by a single load balancer icon. SecureCloud lets you group assets into logical entities, based on tags and other asset properties.
This topic describes what you can see and do after clicking on an asset from anywhere in SecureCloud.
See also Assets.
What Can I See Here?
After selecting an asset, the overview screen appears.
Other details can be viewed by selecting the appropriate menu item. The menu options will vary according the type of asset currently selected.
What Can I Do Here?
-
View overview (default), properties of the asset such as type, security entities, tags and VPC
-
View network configuration This option appears only for VMs, AWS RDS databases and Azure SQL managed instances
-
View the Asset Graph
Asset Overview
This is the default page when displaying the asset. Click Overview from the Asset Menu.
The information pertaining to the select asset is displayed in panels. At the top of the screen, basic information about the asset is shown followed by panels containing additional information. When hovering over fields, you can use the copy-to-clipboard icon to copy/paste of screen information.
Exposure
Indication of whether the asset is exposed to the internet. Two possible values:
- Internet exposed
- No internet
Security Controls
Lists all the security controls and bucket inline policies that control access to this asset, including:
-
 Firewall (AWS firewall, Azure firewall, GCP VPC firewall)
Firewall (AWS firewall, Azure firewall, GCP VPC firewall) -
 Role (AWS role, GCP IAM)
Role (AWS role, GCP IAM) -
 Security group (AWS security group, Azure NSG)
Security group (AWS security group, Azure NSG) -
 Storage security
Storage security -
 Database security
Database security
Click on a security control to see more information.
Properties
The properties shown vary according to vendor and type of asset.
Tags
Lists all tags that apply to this server, in the format key:value or just key.
Violations
All security issues found for the asset are listed according to the type of issue:
- Risky Access
- Policy violations
- Risky ports
- Permissive sources
- Permissive services
- Tag Usage - No tags
Rules
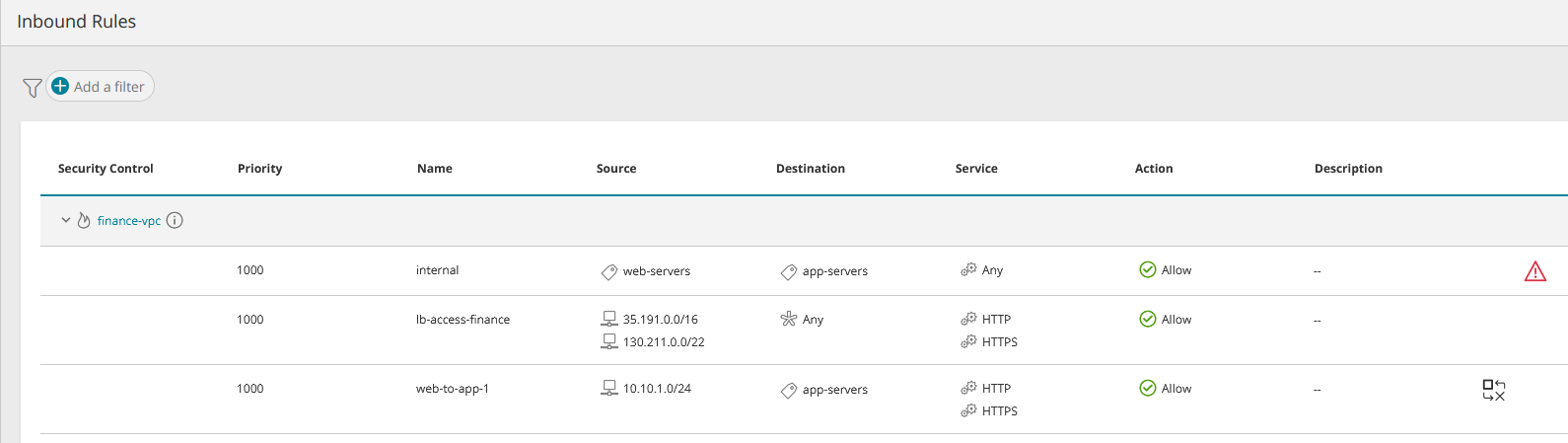
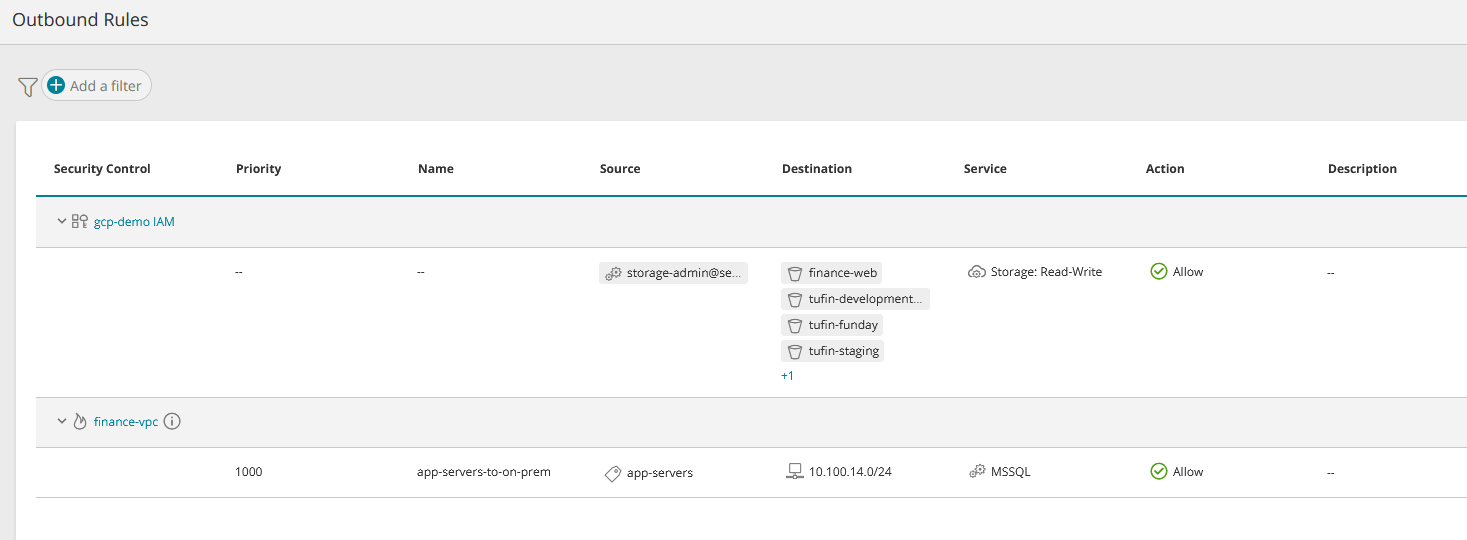
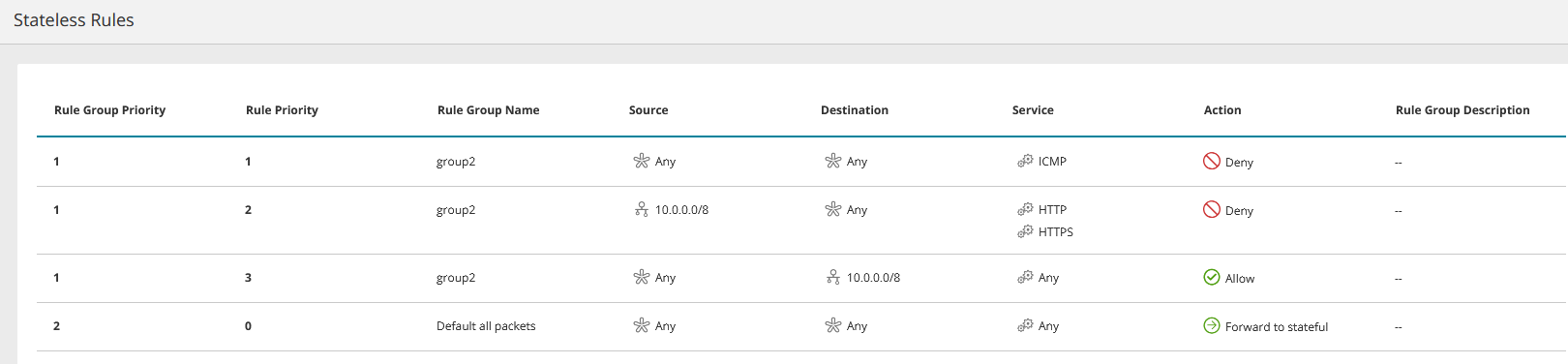
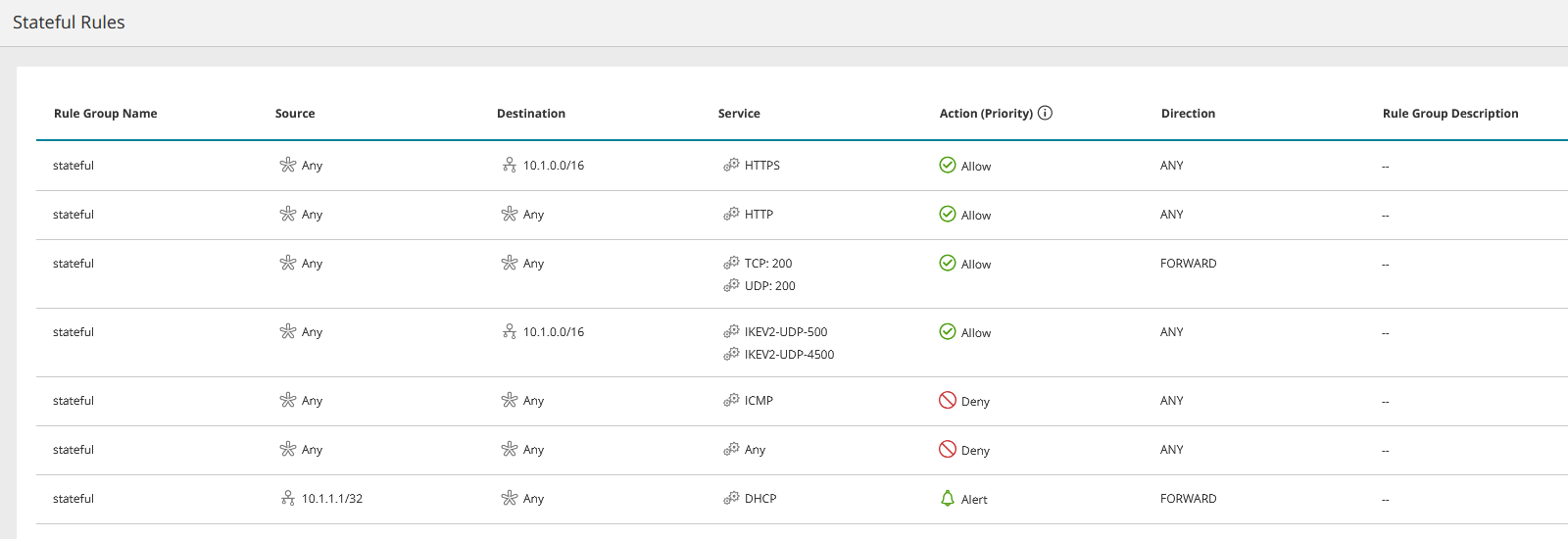
Rules affecting the asset are categorized by the cloud vendor into groups such as inbound/outbound, NAT/network/application, and stateless/stateful and these rule groups appear in the Asset Menu. Examples:
The rules appear under the security control that defines them and the information displayed for the rule will vary from one type of vendor/security control to another. This information may include:
| Field | Comments |
|---|---|
|
Name |
The name of the rule as defined in the security control |
|
Priority |
Sequence of handling the rule as defined in the security control |
| Source | The source specified in the security control. It can vary according to the cloud vendor and security control type e.g. IP, subnet, 'Any', a security group, the security control itself. You can click on some types of source to display more information, such as ID and members. |
| Destination | The destination specified in the security control. It can vary according to the cloud vendor and security control type, e.g. IP, subnet, 'Any', a security group, the security control itself. You can click on some types of destination to display more information, such as ID and members. |
|
Service |
As specified in the security control, this is the communications service of the rule. It can contain multiple values and may include port number e.g. 'Any', TCP, TCP:80 |
|
Action |
Allow / Deny as specified in the security control |
|
Description |
If specified in the security control |
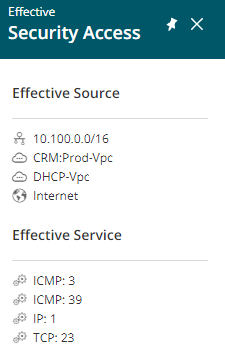
| Access Icon |
Indicates the effective access when considering both the security definitions and the physical network connectivity.
|
|
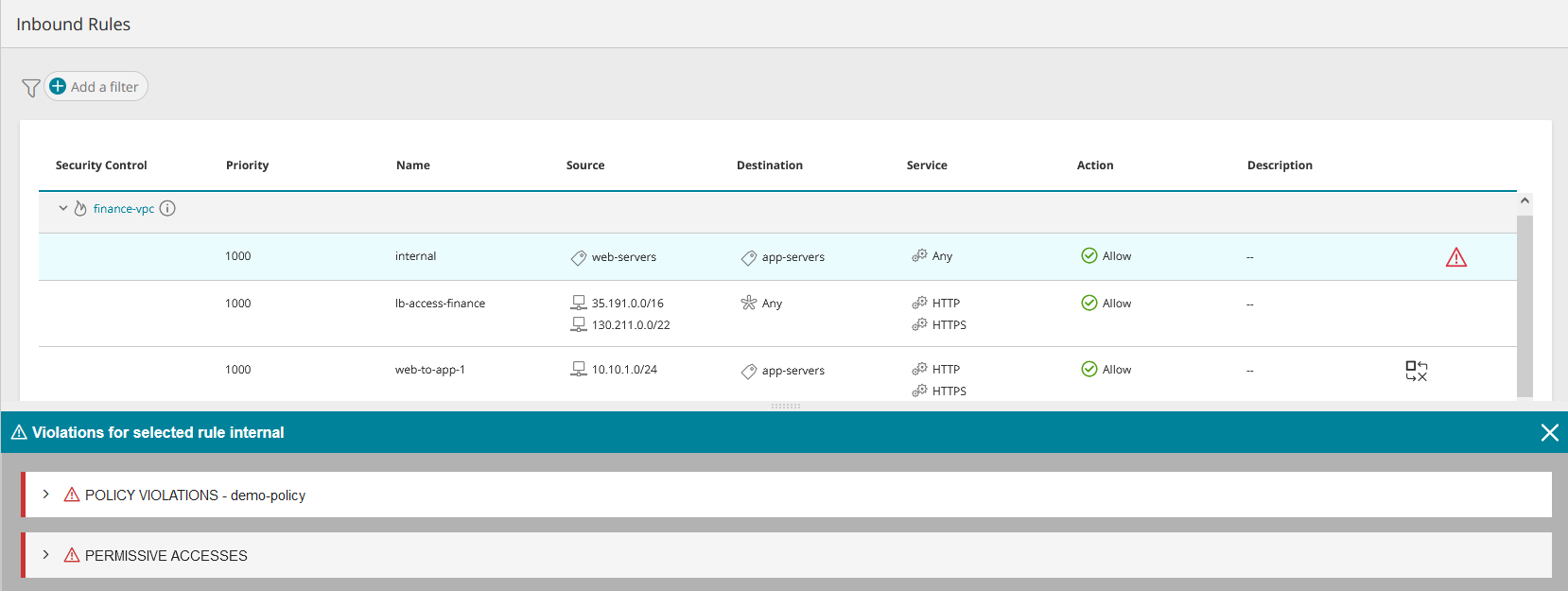
Violations |
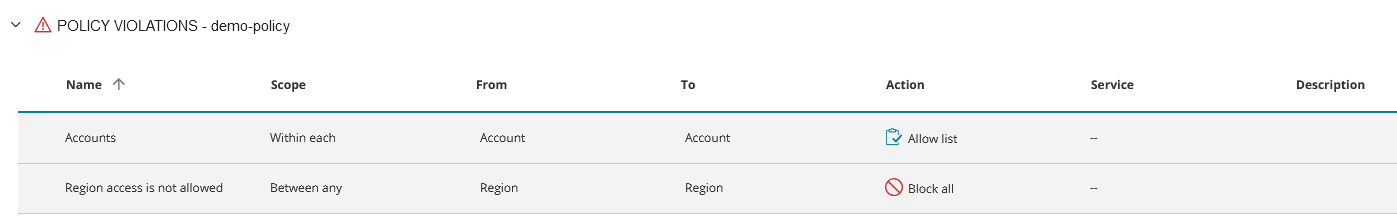
Appears only for incoming rules that violate the security policy you have defined in SecureCloud. If a vendor rule exists that specifies Source=Any, Destination=Any, Service=Any, Action=Deny, then all rules below it are ignored when checking compliance with the cloud security policy. Click A separate line appears for each type of violation:
See Handling Violations. |
|
Options |
Appears only for incoming rules that violate the security policy you have defined in SecureCloud. Click
See Handling Violations. |
Network Configuration
This option appears only for VMs, AWS RDS databases and Azure SQL managed instances.
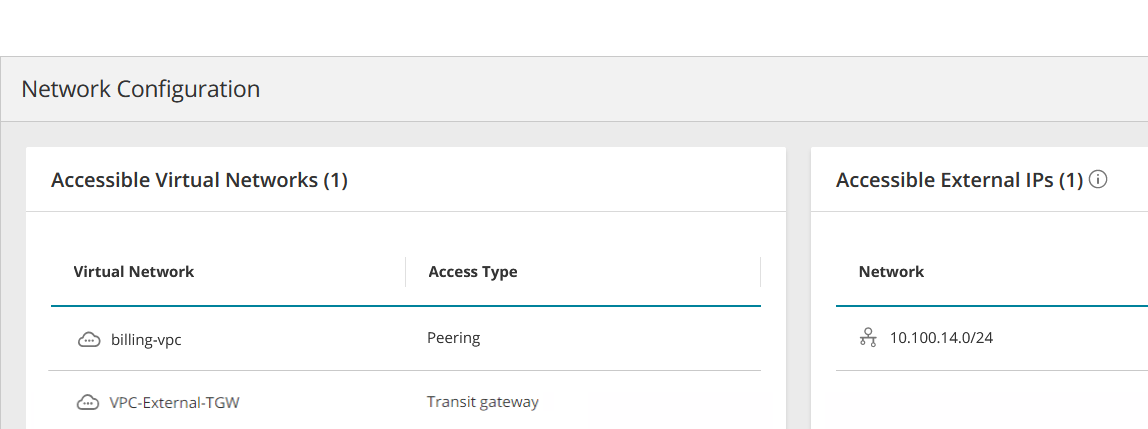
This page shows two kinds of network configuration:
-
Accessible Virtual Networks - Virtual networks configured in your cloud vendor account. Options include Peering, Transit Gateway, and Azure Virtual WAN.
-
Accessible External IPs - Access to IPs outside of your virtual network, through VPN or direct connection.
Click a virtual network to see more details.
Handling Violations
When the violations icon ![]() appears for a rule, there will be options available for handling the violation.
appears for a rule, there will be options available for handling the violation.
Handling Cloud Security Policy Violations
-
Click
 on the rule. A separate line appears for each policy in violation.
on the rule. A separate line appears for each policy in violation. -
Click
 on the desired policy. The line expands and a separate line appears for each rule in violation.
on the desired policy. The line expands and a separate line appears for each rule in violation. -
Hover over the desired rule and click
 to view the available options.
to view the available options. -
Select the desired option:
-
View rule in policy. View the policy in a new browser tab, with the rule highlighted; modify as needed.
-
Add policy rule access. Add a new access definition to the cloud security policy rule (available only for rules defined with action allow/deny list)
-
Edit policy rule. Go to the cloud security policy rule and edit.
-
Remove policy rule. Delete the rule from the cloud security policy.
-
Handling Risky Ports and Permissive Access Violations
-
Hover over the desired vendor rule and click
 to view the available options.
to view the available options. -
Select the desired option:
-
Add exception
-
Delete rule from cloud
-
-
If you selected Delete the rule from cloud , the rule will be removed from your cloud vendor security control.
-
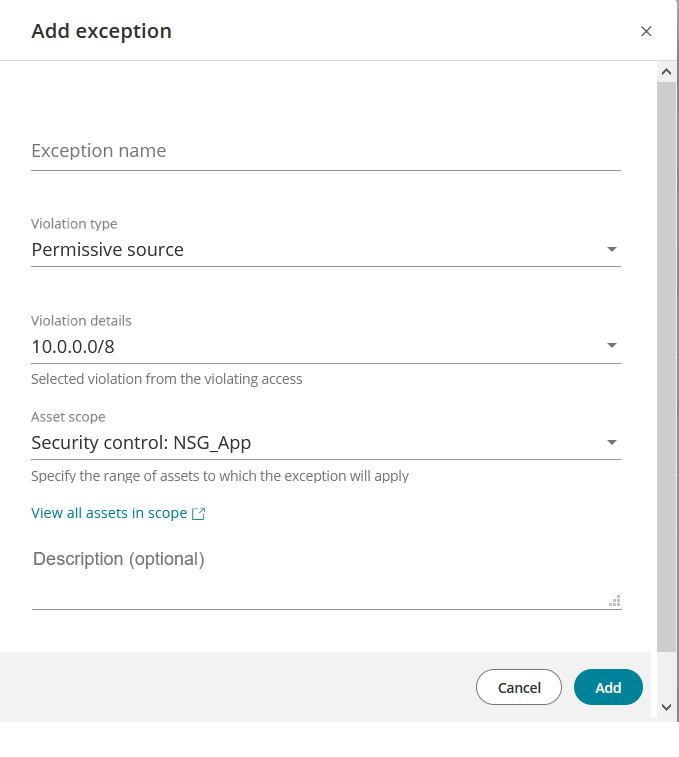
If you selected Add exception, the Add Exception window appears.
Complete the exception details and click Add to save. Once added, the exception appears in Exceptions, where it can be deleted if necessary.
Exception Name: A name of your choice.
Violation Type: Risky port, Permissive source, Permissive service. If more than one type of violation exists for the selected access then select the type of exception you are defining. If only one type of violation exists for the access, it cannot be changed.
Violation Details: The ports, sources or services identified as violations. If more than one violation exists for the selected violation type and access, then select all those appropriate for the exception you are defining. If only one violation exists for this violation type and access, it cannot be changed.
Asset Scope: The assets to be included in the exception. Select one:
-
Security control - all assets to which access is permitted by the security control allowing this access
-
Asset tags - all assets having the exact same tags as this asset
-
Cloud account - all assets in the cloud account in which this asset is located
-
All cloud accounts - all cloud accounts monitored by SecureCloud
You can click View all assets in scope to view all assets that will be affected by this exception
Description: Optional text of your choice.
-
Review Vulnerabilities
Vulnerable assets are those on which a CVE issue has been found.
Common Vulnerabilities and Exposures (CVE) is a list of publicly-disclosed computer security flaws, each of which has a unique CVE ID number. Using vulnerability assessment tools, such as Azure Defender, AWS Integrator, and GCP OS Configuration, SecureCloud identifies assets that have CVEs with an attack vector of type Network. These tools need to be enabled in the vendor account. Additional integrations with other tools can be implemented using APIs that will add the CVEs identified by them to SecureCloud. For more information about additional integrations, contact Tufin support. A CVE will appear in SecureCloud only once, even if identified by different tools.
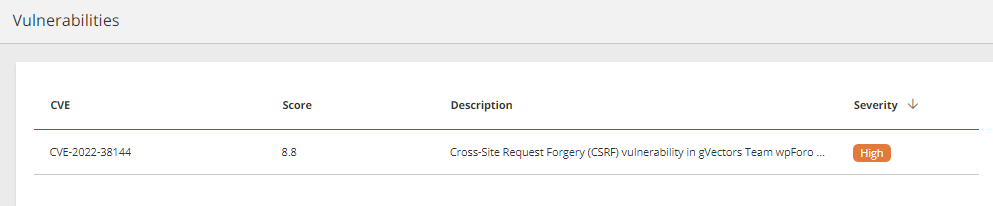
The page lists vulnerable assets with the following information:
-
CVE: Unique ID number for the CVE issue related to this asset.
-
Score: A number between 0 (lowest) and 10 (highest) that is used to prioritize security vulnerabilities.
-
Description: Description of the CVE issue. Hover to see the entire description.
-
Severity: Severity level for the issue: Critical, High, Medium, or Low.
Sensitive Data
SecureCloud identifies assets that have sensitive data exposed to the internet.
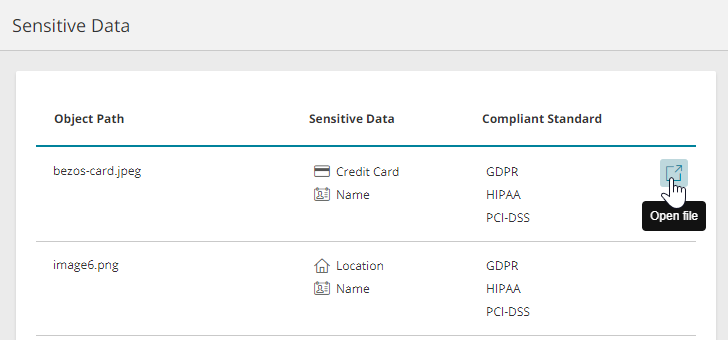
The page lists vulnerable assets with the following information:
-
Object Path: Object that contains sensitive data.
-
Sensitive Data: Type of sensitive data that SecureCloud identified.
-
Compliant Standard: Compliance standards that define sensitive information.
Click the Open File link to view the object.
How Do I Get Here?
- Click the asset name from anywhere in SecureCloud. If unsure, start with Assets.